I’m here today to relate a story about my friend who had his bike stolen last September from Gunwharf Quays. It was in broad daylight in a busy area with lots of shoppers and people walking close by.

How did this happen? The answer is simple – the lock my friend had used was little more than a piece of a wire. Quickly and stealthily cut with a pair of pliers.

Do not make the same mistake my friends, get a decent U-lock or D-Lock such as this. This lock conforms to the Sold Secure “Silver” certification standard – which is an independent lock testing standard. You want to aim for “Silver” or above when it comes to choosing a lock for your bike. Another good lock is this one from Kryptonite.

May 2019 Update: this is the lock that WG has been using for the last year – tough and compact and Sold Secure Gold rated:

If I’m cycling somewhere like the New Forest where I’m not sure that cycle lock hoops are available then I will take a thick cable lock like this one below so it’s easier to attach to posts and fences etc:

At the very least when locking your bike you MUST put the lock through the rear wheel, large triangle of the frame and loop it around a fixed bike post.
So, what to do if your bike is actually stolen? Sadly not that much. You can report it to the Police and if they recover it they might contact you. Some Police forces have a Twitter account where they publicize recovered bikes (like this one).
In my friends case above I actually located the bike on Gumtree a few days after it had been stolen. What I did was to set-up a search alert using the keywords and location of the theft (in this case “mountain bike” and “within 5 miles of Southsea, Hampshire”). Normally the thief will live locally (these unfortunate people normally sell them on to fund a drug habit or other addiction).
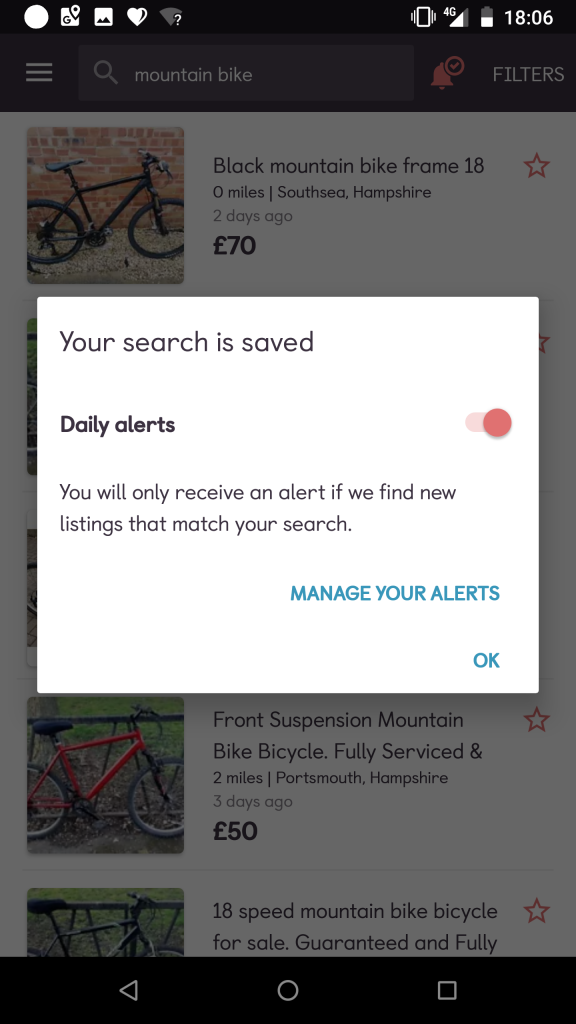
After I set-up a daily search alert on Gumtree I made sure to check the alerts every day for a week… Sure enough a few days later his bike appeared! It was being sold by a guy in Southsea – within about a mile of Gunwharf Quays. The seller’s name was “Jordan” and I contacted the guy feigning interest.
I sent my friend the link and he reported it to the Police. Sadly the Police probably would not be able to recover it and are generally have other more important crimes to deal with :/
That was no comfort to my friend but he is of a chilled, live-and-let-live disposition so it was cool with him.
He did relate one tale of someone finding their stolen bike on Gumtree, arranging to take a test ride of it.. and then cycling off into the distance, re-united with their bike once more. I can’t ever condone that though since it might incur a violent encounter with the original theif.
Stealing your own bike back though? I’ve love to see a video of such an incident – complete with a Go-Pro rear-facing camera capturing the look on the face of the original miscreant 😉
Further reading: How Not to Get Your Bike Stolen